CEH 3-Scanning Networks
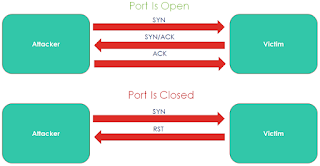
↑ Previous Page Next Page What is Scanning? Scanning is a process of identifying network and service related information by communicating with the target. Scanning helps in identifying IP/Host-names, Ports, Services running on ports, Live hosts, Vulnerable services running on the target network. Disclaimer: The articles provided on HackWithV is purely for informational and educational purpose only, and for those who are willing and curious to know & learn about Ethical Hacking, Security and Penetration Testing. Anytime the word "Hacking" that is used on this site shall be regarded as Ethical Hacking. Types of Scanning: Network Scanning: Identifying the number of computers on the network. Ping Sweep Arp Scan Port Scanning: Listing open ports and services running on those ports. SYN Scan/Stealth Scan/Half-Open Scan TCP Connect Scan ACK Scan/Firewall Detection Scan XMAS Scan FIN Scan NULL Scan OS Detection Scan