Computer Networks Basics (Part 1)
Computer Networks:
- Network is invented to communicate two or more computers together.
- A network is a group of two or more computer systems or other devices that are linked together to exchange data.
- In networks, computing devices exchange data with each other using data links between nodes.
- These data links are established with the help of cable media(Ethernet wires) or wireless media(WiFi).
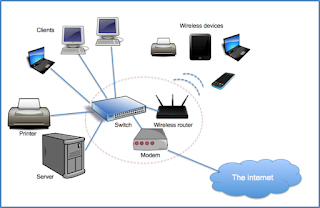
fig1: Basic Network
Disclaimer: The
articles provided on HackWithV is purely for informational and
educational purpose only, and for those who are willing and curious to
know & learn about Ethical Hacking, Security and Penetration
Testing. Anytime the word "Hacking" that is used on this site shall be
regarded as Ethical Hacking.
Types of Networks:
Personal Area Network (PAN):
A personal area network is a computer network organized around an individual. Personal area networks typically involve mobile devices. Personal area networks can be wired or wireless. These networks generally cover a network range of 10 meters (about 30 feet).Local Area Network (LAN):
A LAN is a network that connects computers and devices in a limited geographical area such as a home, school, office building.Wide Area Network (WAN):
A WAN is a computer network that covers a large geographic area such as a city, country, or spans even intercontinental distances. A WAN uses a communications channel that combines many types of media such as telephone lines, ethernet cables, optical fibers, etc.Metropolitan Area Networks (MAN):
Metropolitan area Network covers a larger area than that of a LAN and smaller area when compared to WAN. MANs rarely extend beyond 100km and comprise a combination of different hardware and transmission media.Wireless Local Area Network (WLAN):
Wireless local area networks provide wireless communication over short distances using radio or infrared signals instead of traditional network cabling. WLANs are built by attaching a device called the access point to the edge of the wired network. Clients communicate with the AP using a wireless network adapter similar in function to a traditional Ethernet adapter.Virtual Private Network (VPN):
The virtual private network is an overlay network in which some of the links between nodes are carried by virtual circuits in the network instead of physical wires. The data link layer protocols of the virtual network are said to be tunneled through the network.
How Different Computers Communicate?
Ans: Using a standard called OSI Model. This standard is followed when the device manufacturing. All networking devices follow this standard.
OSI Model:
- OSI (Open Systems Interconnection) is a reference model for how applications communicate over a network.
- The main concept of OSI is that the process of communication between two endpoints in a network can be divided into seven distinct groups of related functions or layers.
- Each communicating user or program is on a device that can provide those seven layers of function.
- The seven Open Systems Interconnection layers are:
fig2: OSI Model
Physical Layer:
This layer conveys the bit stream across the network either electrically, mechanically or through radio waves. The physical layer covers a variety of devices and mediums, among them cabling, connectors, receivers, transceivers and repeaters.Data Link Layer:
This layer sets up links across the physical network, putting packets into network frames. This layer has two sublayers the logical link control layer and the media access control layer (MAC). MAC layer types include Ethernet and 802.11 wireless specifications.
Network Layer:
This layer handles addressing and routing the data. To transfer it from the right source to the right destination. The IP address is part of the network layer.
Transport Layer:
This layer manages packetization of data, then the delivery of the packets, including checking for errors in the data once it arrives. On the internet, TCP and UDP provide these services for most applications.
Session Layer:
The session layer controls the connections between computers. It establishes, manages and terminates the connections between the local and remote application.
Presentation Layer:
This layer is usually part of an operating system (OS) and converts incoming and outgoing data from one presentation format to another for example, from clear text to encrypted text at one end and back to clear text at the other.
Application Layer:
The application layer of the OSI model interacts with the end user. Protocols at this layer handle the requests from different software applications. If a web browser wants to download an image, an email client wants to check the server, and a file-sharing program wants to upload a movie, the protocols in the application layer will process those requests.
Network Components and Functions:
- Devices: Computer devices, such as a CD-ROM drive or printer, that is not part of the essential computer. Examples of devices include disk drives, printers, and modems.











Comments
Post a Comment