CEH 12- Evading IDS, Firewalls & Honeypots
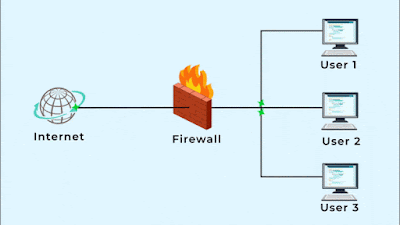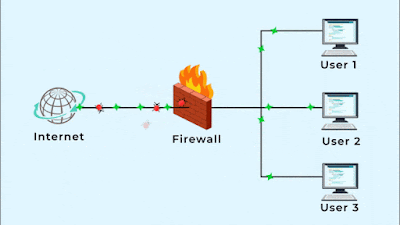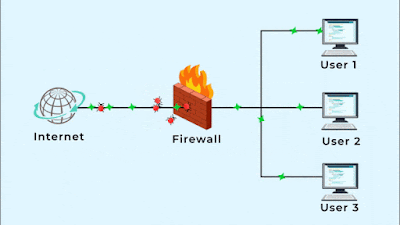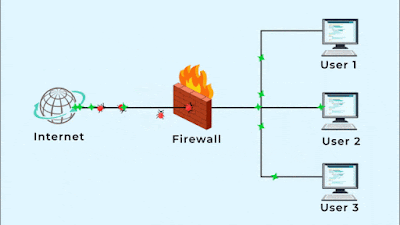
What is a Firewall?
- A firewall is a software or hardware device.
- It secures the internal trusted network form the intruders by monitoring and controlling incoming and outgoing network traffic based on predetermined security rules.
- A firewall typically establishes a barrier between a trusted internal network (LAN) and an untrusted external network(Internet).
Disclaimer: The
articles provided on HackWithV is purely for informational and
educational purpose only, and for those who are willing and curious to
know & learn about Ethical Hacking, Security and Penetration
Testing. Anytime the word "Hacking" that is used on this site shall be
regarded as Ethical Hacking.
- Types of Firewalls:
- Packet filter firewalls
- Circuit-level gateways
- Application-level gateways
- Stateful inspection firewalls
1. Packet Filter Firewalls:
- Packet filtering firewall is used to control network access.
- By monitoring outgoing and incoming packets.
- Allowing them to pass or halt based on the source and destination IP addresses, protocols and ports.
- The packet filtering firewall examines the header of each packet based on a specific set of rules.
2. Circuit-level gateways:
- Circuit level gateways work at the session layer of the OSI model.
- It monitor TCP handshake, to determine whether a requested session is legitimate or not.
- Information passed to a remote computer through a circuit level gateway
firewall appears to be originated at user’s computer. - Circuit level gateways are relatively inexpensive and have the advantage of hiding information about the private network.
- On the other hand, they do not filter individual packets.
3. Application-level gateways:
- Application-level gateways can filter packets at the application layer of the OSI model.
- Application-level gateways examine traffic and filter on application specific commands such as HTTP, POST and GET.
- This works on the application layer of the TCP/IP Model.
4. Stateful inspection firewalls:
- Stateful inspection firewalls combine the aspects of the other three types of firewalls.
- They filter packets at the network layer for IP header, to determine whether session packets are legitimate, and they evaluate the contents of packets at the application layer.
- Traffic is filtered at three layers based on a wide range of the specified application, session, and packet filtering rules.
Firewall Products:
What is a Honeypot?
- A honeypot is a computer security mechanism set to detect or deflect attempts at unauthorized access to the information systems.
- In other words, it is a simple trap to catch the hackers.
- In honeypots, we will emulate the required devices in an environment and we will let attackers come there and try to perform attacks.
- But meanwhile, we will get the identity of the attacker.
- So that we can take action against attacks.
- Honeypots are of two types:
- Low Interaction Honeypot
- High Interaction Honeypot
1. Low Interaction Honeypot:
- Low interaction honeypots allow only limited interaction for an attacker.
- All services offered by a low interaction honeypot are emulated.
- Thus, these are not themselves vulnerable and will not be infected by the exploit attempted against the vulnerability.
2. High Interaction Honeypot:
- High interaction honeypots make use of the actual vulnerable service or software.
- These are usually complex as they involve real vulnerable operating systems and applications.
- In this type of Honeypots, nothing is emulated everything is real and provide a far more detailed picture of how an attack or intrusion progresses or how a particular malware executes in real-time.
List of honeypots:
- Database Honeypots
- Anti-honeypots
- Service Honeypots
- Web honeypots
What is an Intrusion Detection System (IDS)?
- An intrusion detection system (IDS) is a device or software application.
- It monitors network or computer system operations for malicious activities, policy violations and reports to a controlling station.
- Capabilities of IDS:
- Monitoring the operation of routers, firewalls, key management servers and files that are needed by other security controls aimed at detecting, preventing or recovering from cyber attacks.
- Including an extensive attack signature database against which information from the system can be matched.
- Recognizing and reporting when the IDS detects that data files have been altered.
- Generating an alarm and notifying the security operations team when there is a security breach.
- IDS detection methods:
- Signature-based
- Behaviour-based
- Types of IDS:
- Network-based Intrusion Detection System.
- Host-based Intrusion Detection System.
1. Network-based Intrusion Detection System(NIDS):
- NIDS is an IDS which can be configured on a network to monitor intrusions.
- This will notify the administrators about any possible signature match of attacks.
2. Host-based Intrusion Detection System(HIDS):
- HIDS are the IDS systems which will be configured on the standalone machines.
- It will only detect intrusions for that particular machine.
HIDS might detect which program accesses what resources and discover malicious attempts. - For example, a word-processor has suddenly started modifying the system password database, which can be considered as a malicious attempt on sensitive data stored on the host machine.
List of IDS:
- Snort IDS
- Cisco ASA Security Agent
- McAfee Security Agent
- Palo Alto
- SonicWall
- Juniper
Whats is an Intrusion Prevention System (IPS)?
- An Intrusion Prevention System (IPS) is a network security/threat prevention
technology. - It examines network traffic flows to detect and prevent vulnerability exploits.
- Vulnerability exploits usually come in the form of malicious inputs to a target application or service that attackers use to interrupt and gain control of an application or machine.
- Some of the actions perfromed by IPS as follows:
- Sending an alarm to the administrator.
- Dropping the malicious packets.
- Blocking traffic from the source address.
- Resetting the connection.
- Types of IPS:
- Host-based Intrusion Prevention Systems.
- Network-based Intrusion Prevention Systems.
1. Host-based Intrusion Prevention Systems(HIPS):
- Host-based Intrusion Prevention Systems are used to protect both servers and workstations through software that runs between your system's applications and OS kernel.
- The software is preconfigured to determine the protection rules based on intrusion and attack signatures.
- The HIPS will catch suspicious activity on the system and then depend on the predefined rules, it will either block or allow the event to happen. HIPS monitor activities such as application or data requests, network connection attempts, and read or write attempts.
2. Network-based Intrusion Prevention Systems(NIPS):
- Network-based Intrusion Prevention System is a solution for network-based security.
- NIPS will intercept all network traffic and monitor it for suspicious activity and events, either blocking the requests or passing it.
- One interesting aspect of NIPS is that if the system finds an offending packet of information it can rewrite the packet so that attempt for the attack will fail.
- But the organization can mark this event to gather evidence against the intruder, without their knowledge.
Mitigations:
- Perform an in-depth analysis of network traffic to detect all possible threats.
- Shut down switch ports associated with the known attack hosts.
- Use a traffic normalizer to remove potential ambiguity from the packet stream before it reaches to the IDS.
- Harden the security of all communication devices such as modems, routers, switches, etc.





Comments
Post a Comment