Web Application Password Cracking
In this article, we are going to crack the user password in a web application with the help burpsuite tool.
Disclaimer: The articles provided on HackWithV is purely for informational and educational purpose only, and for those who are willing and curious to know & learn about Ethical Hacking, Security and Penetration Testing. Anytime the word "Hacking" that is used on this site shall be regarded as Ethical Hacking.
What is Password Cracking?
-
In password cracking, hackers use a different kind of attacks to know the
target computer/website login password so that they can gain complete
access.
Types of Password Cracking
- Password Guessing: Not a technique, but usually the first thing that every criminal will try to do.
- Brute Force Attack: All possible permutations & combinations of the keyboard are tried as the victim's password. All passwords have to be some permutation or combination of victim's keyboard characters.
- Dictionary Based Attack: All words in the dictionary are tried as the victim’s password.
- Syllable attack: Combination of both, brute force attack and a dictionary attack. This is often used when the password is a nonexistent word.
- Default Passwords: Manufacturers configure the hardware or software with default passwords and settings. We can get default passwords online for devices (http://defaultpassword.us/).
- Data Sniffing: Data sniffer to record passwords being sent across the LAN network in plaintext format.
In this article we are going to use dictionary based attack to crack the password of web application user.
Practical:
- Target Web Application: OWASP JUICE SHOP
- Target User : vinay@gmail.com
- Tools : Kali Linux, Firefox, Burpsuite, Docker Container.
Step 1:
- Open OWASP Juice Shop.
- Click on the Account, Login.
- Try to login with Email(vinay@hackwithv.com) and Password(12345678).
- The server throws an error "Invalid email or password."
Step 2:
- Now turn on the burpsuite, goto "proxy tab", goto "intercept" subtab, turn on the "Intercept on".
- In firefox setup burp proxy with help of foxyproxy.
- Click on foxyproxy icon, then click on burp (already configured to brup proxy).
Step 3:
- Now try to login with same email and password.
- The login request is captured by the burpsuite.
- Send the login request to Intruder by right clicking on request, then click on "send to Intruder".
Step 4:
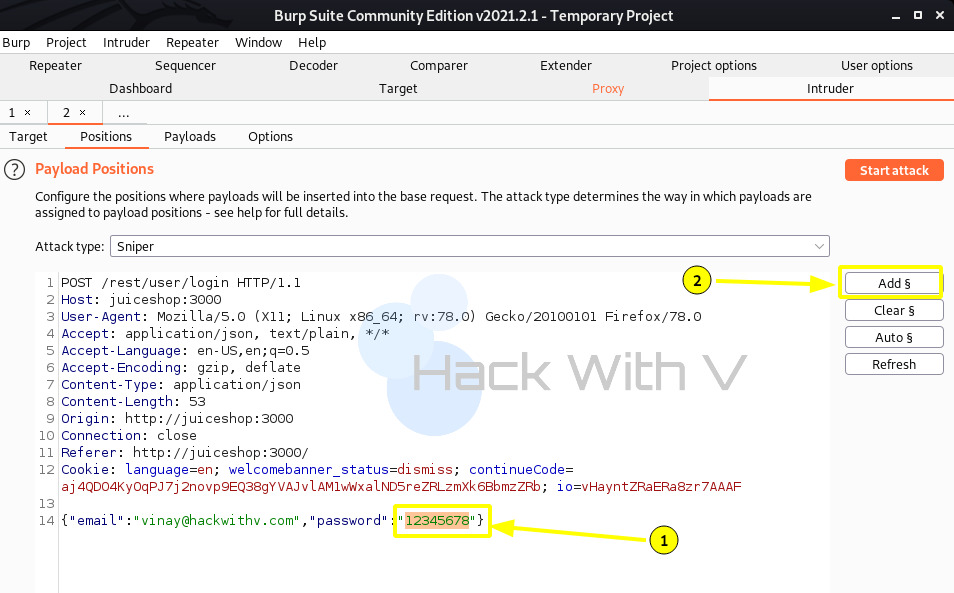
- Now click on "Intruder" tab, goto click on "positions", click on "clear" button.
- Select the password value and click on the "add" button.
- Copy the list of passwords from a file.
- In brupsuite, in Intruder tab, in payload sub-tab, in payload options click on the paste. Then uncheck the URL-Encoding.
- Click on "Start Attack", a new window will be opened as shown below.
- After completion of attack, by analyzing the response "status code" and "length" we got only one is different from other payload as shown in below figure.
Step 5:
- Now try to login with these credentials, Boooom we have success logged into vinay@hackwithv.com account.
Mitigations:
- Use stronger authentication methods.
- Enable security auditing to help monitor attacks.
- Limit the login attempts to 3-5 times.
















Thank you I am coming soon with more post.
ReplyDeleteThank you
ReplyDelete